Perimeter Intrusion
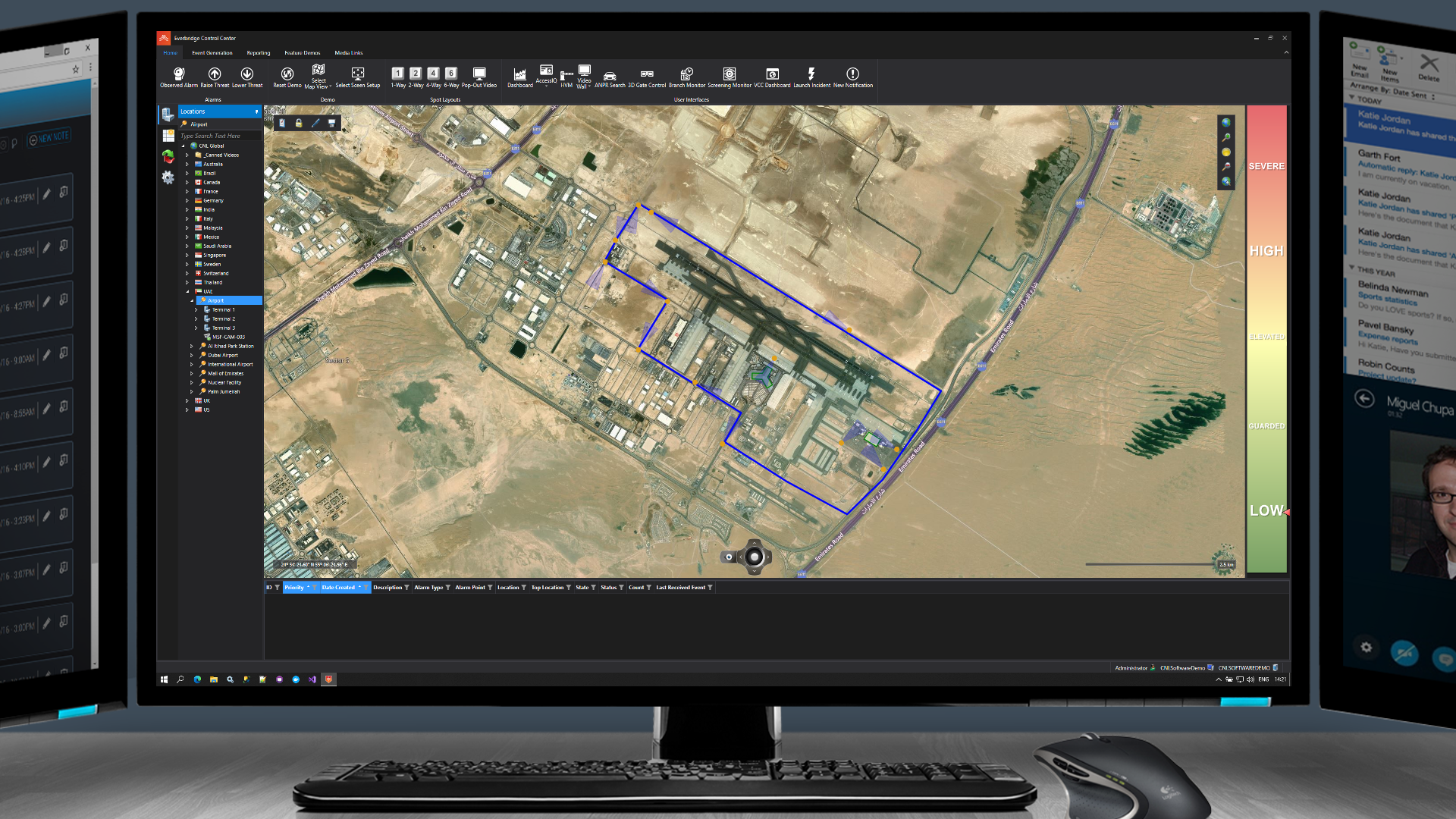
A single pane of glass is used to manage all security systems across all locations. Different mapping including GIS, CAD, 2D and 3D is used for easy navigation and optimal situational awareness.
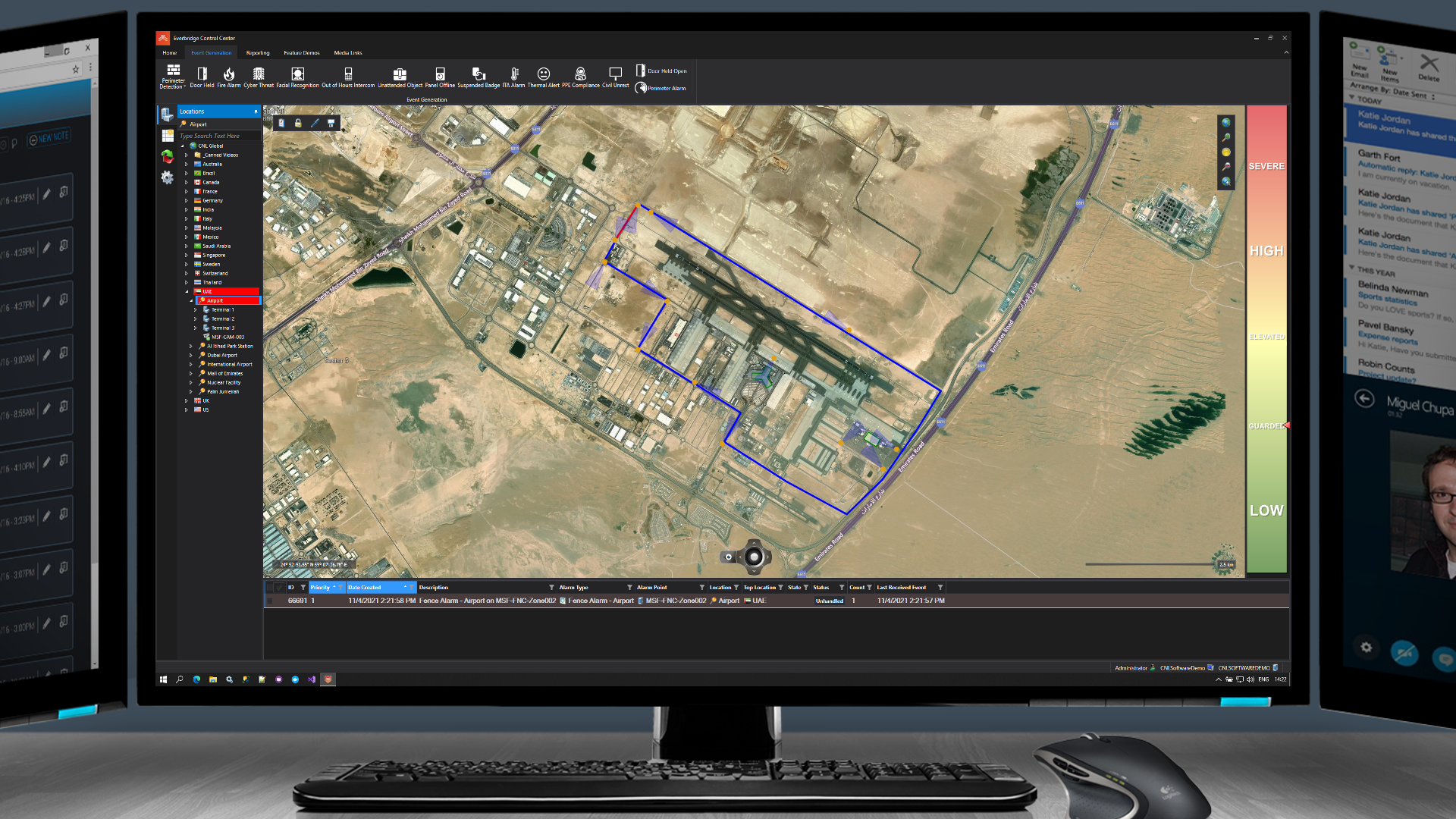
Alarms from all the different security systems are shown in the unified alarm stack. Here, an alarm from the perimeter fence is shown, prompting the user to take action.
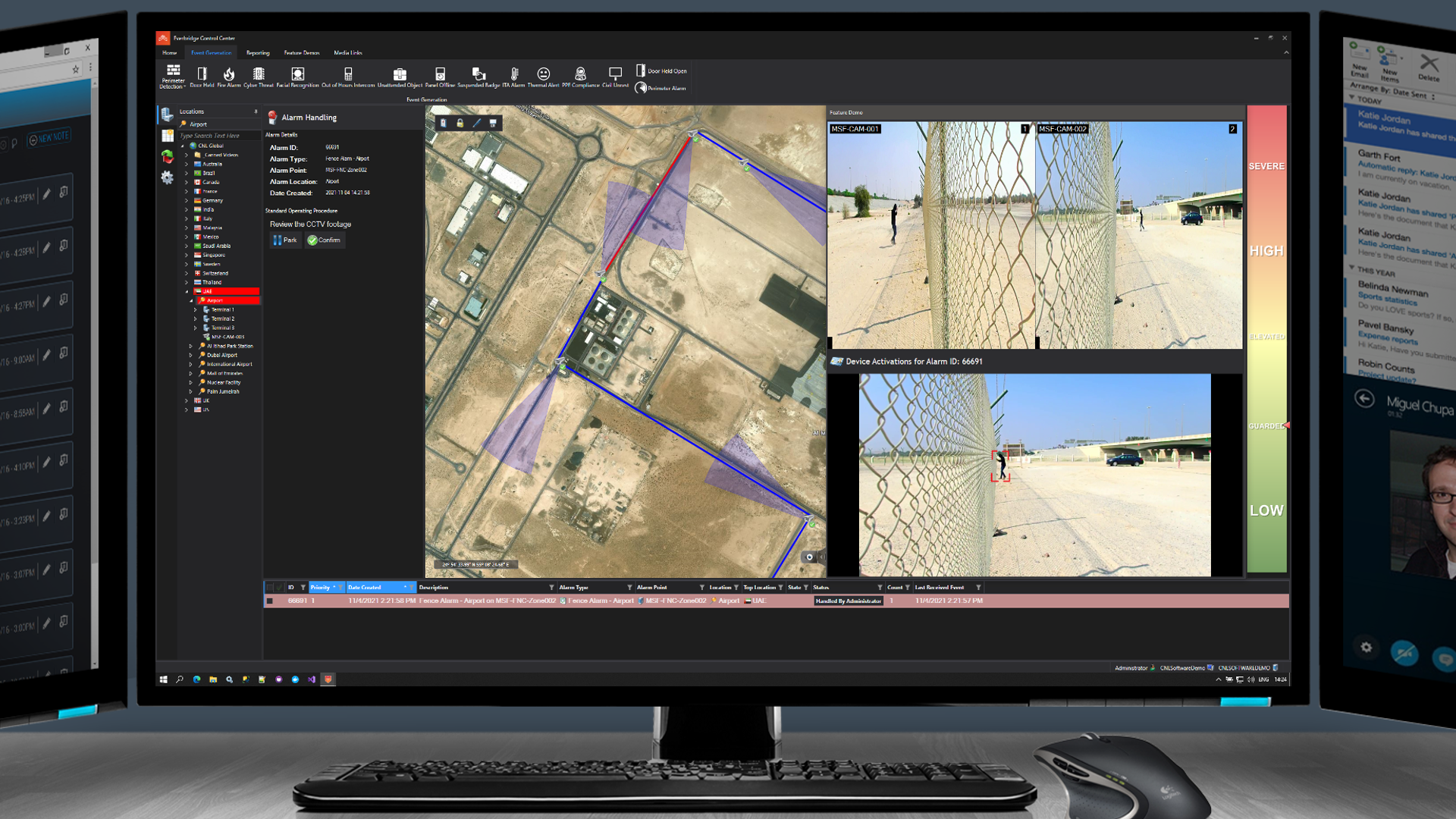
Clicking the alarm automatically pulls up all relevant contextual information. Live and recorded video is shown, no matter which video system is used, and step-by-step instructions are presented as per the defined Standard Operating Procedure (SOP).
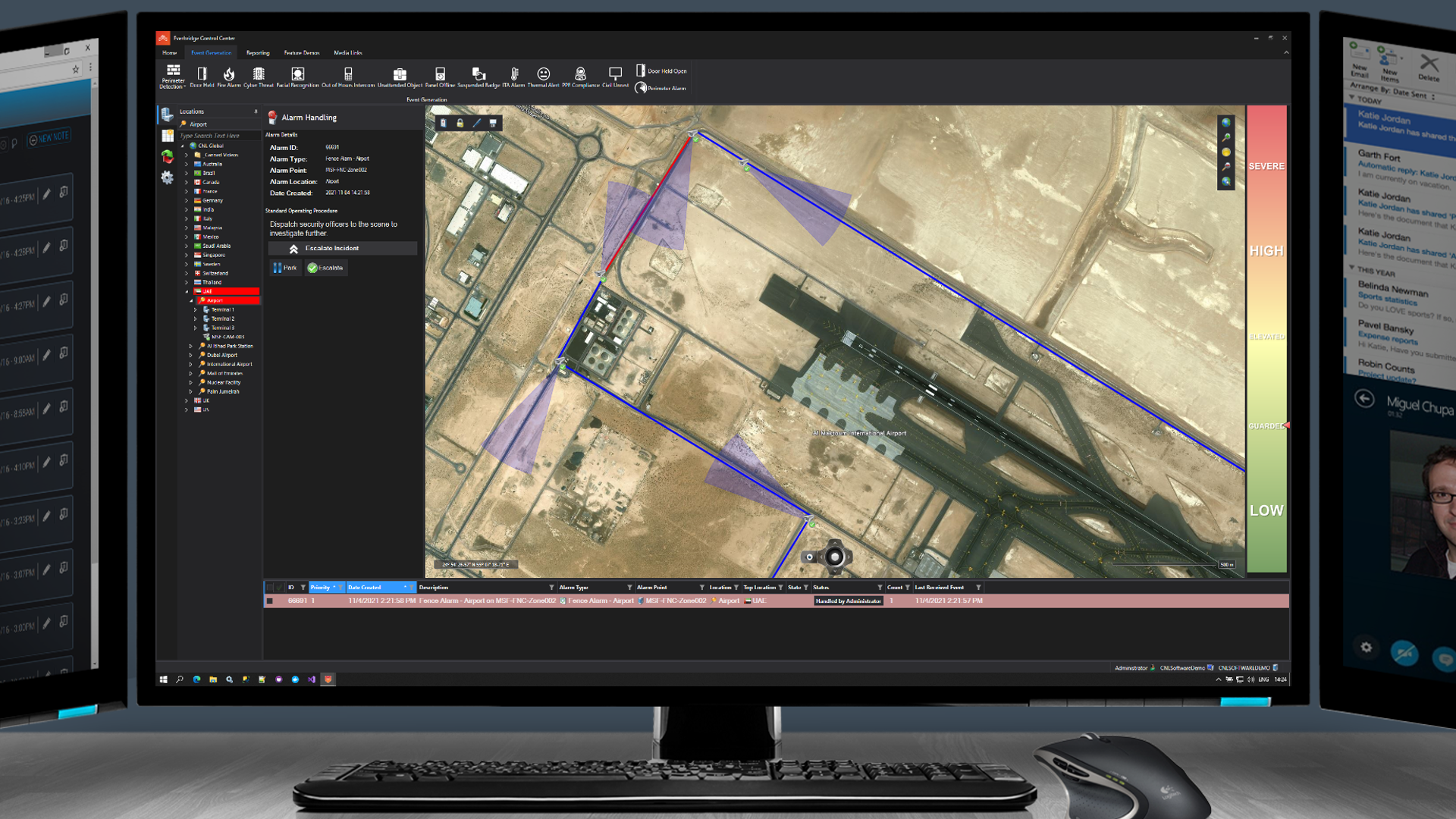
Once the alarm is confirmed as a real threat, the user is prompted to escalate the incident to the local response team. All aspects of the response process are fully configurable as per client SOPs.
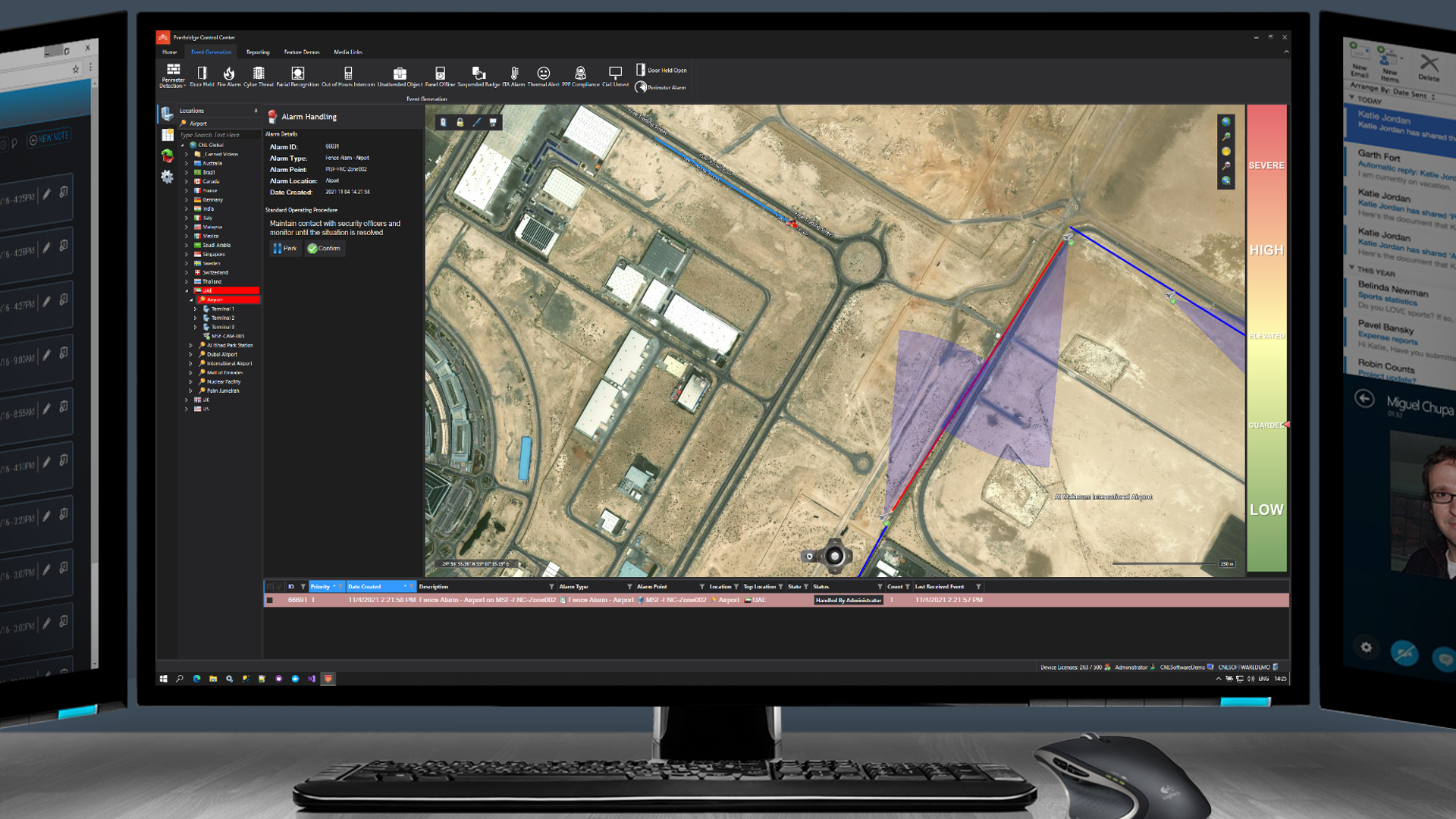
The response team is dispatched via their mobile application and tracked via GPS. The user is instructed to maintain radio communication with the team until they arrive at location.
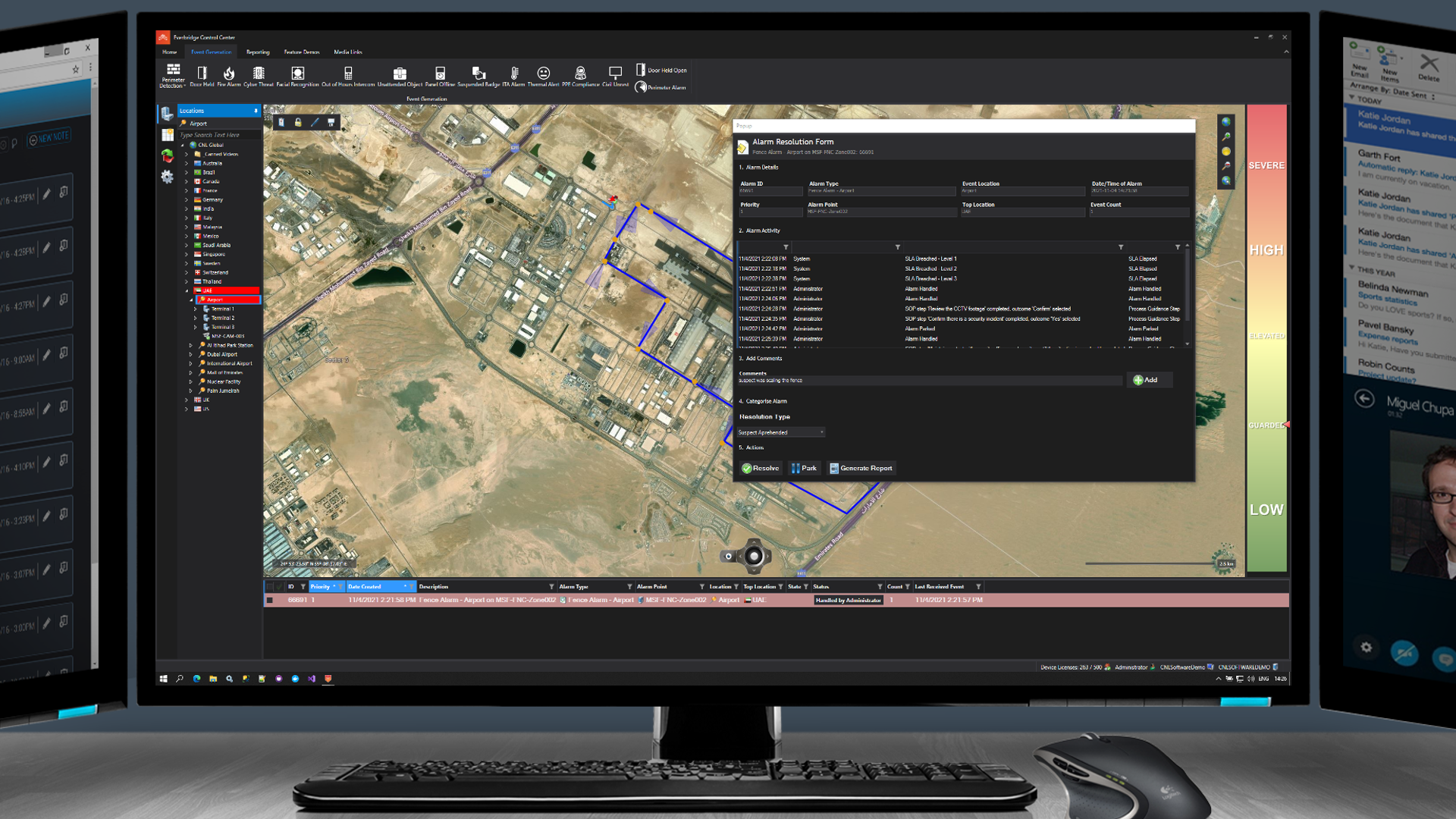
Once the response team confirms they have apprehended the suspect, the user is prompted to enter any additional notes and to close the incident.
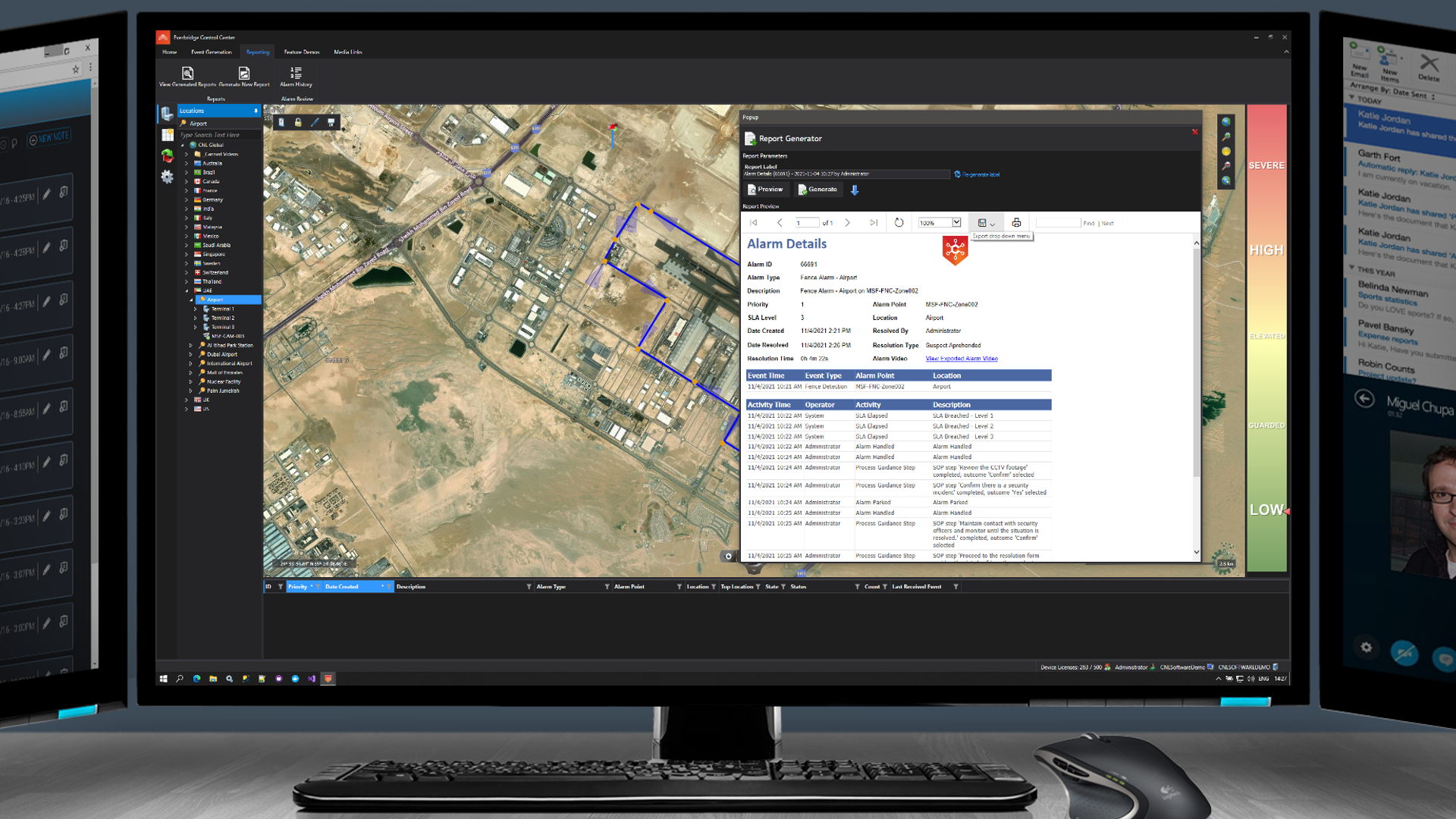
Every input and every action taken is automatically timestamped and logged in the secure audit trail and used for the fully customizable after-action report, which are automatically distributed along with any evidence taken such as screenshots or video recordings.